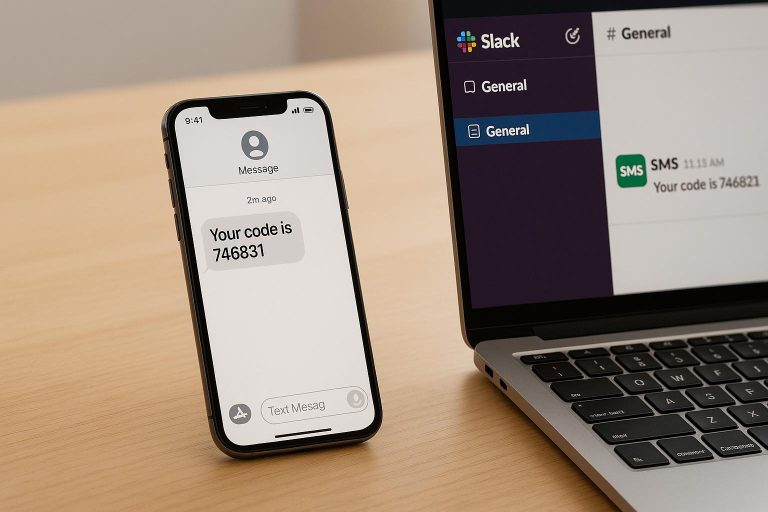
What Is SIM Swap Detection?
SIM swap detection is a security process that identifies when someone transfers a phone number to a different SIM card without permission. This helps prevent fraudsters from accessing sensitive accounts like banking, email, or social media by intercepting SMS-based two-factor authentication codes.
Key Points:
- What is SIM Swap Fraud? Attackers trick mobile carriers into transferring your phone number to their SIM card, enabling access to accounts tied to your number.
- Why it Matters: SIM swap attacks can lead to financial losses, identity theft, and account takeovers. In 2024, SIM swap fraud increased by over 1,000%.
- How It Works: Fraudsters collect personal info, impersonate you to your carrier, and take control of your phone number to intercept security codes.
- Detection Methods: Systems monitor unusual activity like frequent SIM changes, location anomalies, and behavioral patterns to flag potential fraud.
- Prevention Tips: Use strong PINs for your carrier, avoid SMS-based authentication, and enable SIM locks or port protection.
Quick Prevention Tips:
- Use app-based two-factor authentication instead of SMS.
- Set up a unique PIN for your wireless account.
- Monitor your accounts for unusual activity.
- Contact your carrier immediately if your phone loses service unexpectedly.
SIM swap detection is essential to protect your accounts and personal information from growing cyber threats.
What Is a SIM Swap Attack, and How Can You Prevent It?
How SIM Swap Attacks Work
SIM swap attacks follow a clear and exploitable pattern, which makes identifying them early absolutely critical. Understanding how these attacks unfold is key to protecting yourself and your accounts.
The Process of a SIM Swap Attack
It all starts with information gathering. Fraudsters collect personal details through methods like phishing emails, data breaches, or social engineering. These details will later be used to impersonate the victim.
"SIM swapping fraud typically begins when the fraudster acquires sensitive information about the victim, such as their national ID, phone number, and card details." – Group‑IB [8]
Once they’ve gathered enough information, the attackers move to the next stage: social engineering. They contact your mobile carrier, pretending to be you. Their goal? Convince the carrier to transfer your phone number to a SIM card they control. Common excuses include claims of a lost phone, a damaged SIM card, or the need to activate service on a new device. Armed with your personal details, they appear convincing enough to bypass basic security checks.
While mobile carriers have measures in place to prevent such fraud, attackers often find ways around them [8]. In some cases, they even bribe carrier employees, offering cryptocurrency as payment for transferring numbers [7].
The final step is the most damaging. Once your number is transferred, the fraudster gains control over all calls and texts meant for you. This includes two-factor authentication codes, which they use to break into your email, financial accounts, and other sensitive services.
These carefully orchestrated steps can lead to immediate and severe consequences for victims.
Impacts of SIM Swap Fraud
The fallout from a SIM swap attack can be swift and devastating. Financial losses are often the first and most visible impact. Victims can lose access to bank accounts, investment platforms, and cryptocurrency wallets within hours. For instance, in 2023, four men in Florida were convicted of stealing over $509,475 in cryptocurrency through SIM swapping. Similarly, an Arizona man was found guilty of stealing nearly $1 million in cryptocurrency, while a group led by a Chicago man allegedly stole $400 million by targeting over 50 victims [9].
But the damage doesn’t stop at financial accounts. Attackers can intercept SMS-based two-factor authentication codes, reset passwords, and take over accounts across multiple platforms. Email accounts are particularly valuable since they’re often used for password recovery [5].
The rapid pace of these attacks makes them especially dangerous. Beyond financial theft, identity theft is another major risk. With control over your phone number, fraudsters can apply for credit cards, loans, and other financial products in your name. The resulting damage to your credit score and financial reputation can take months – or even years – to repair.
For businesses, the stakes are even higher. A compromised employee account can lead to data breaches, regulatory fines, and a loss of customer trust. Just look at the November 2023 attack on Bankers Life and Washington National Insurance, which exposed the data of over 66,000 customers [6].
The psychological toll on victims is another layer of harm. Losing control of your digital identity can cause lasting anxiety and erode trust in online services. Recovery is often slow and complex, especially in cases involving cryptocurrency theft, where funds are typically irretrievable. Unlike credit card fraud, where charges can be reversed, proving SIM swap fraud and recovering losses can be a lengthy and frustrating process.
How SIM Swap Detection Works
SIM swap detection systems function like vigilant security guards, constantly monitoring for unusual activity involving phone numbers and SIM cards. By layering various technologies, these systems aim to identify and stop fraudulent actions before attackers gain full access to a target’s accounts.
Detection Methods and Technologies
The most effective systems keep an eye on recent SIM changes in real time. When someone requests to transfer a phone number to a new SIM card, these systems flag the activity for review. They do this by querying carrier databases to confirm the SIM card’s status and history.
Device analytics are another crucial tool. These systems analyze data like device fingerprints, location information, and connection behaviors. For instance, if a phone number is suddenly active on an unfamiliar device or in an unexpected location, it raises a red flag.
Behavioral pattern analysis adds an extra layer of security. These systems establish a baseline of normal user behavior – such as typical login times, frequently used services, and usual communication habits. If there’s a significant deviation from these patterns, especially after a SIM swap, the system can step in to block suspicious actions.
Artificial intelligence takes detection a step further by analyzing historical data for subtle signs of fraud. This allows the system to catch early warning signals that might otherwise go unnoticed.
Some advanced systems even offer subscription-based alerts. These notify businesses in real time whenever a SIM card’s status changes, enabling immediate action against potential threats. By integrating real-time telecom data, these systems can detect fraud as it happens, rather than after the damage is done. This real-time capability lays the groundwork for deeper analysis, which we’ll explore next.
Data Used in SIM Swap Detection
To determine whether a SIM swap is legitimate or fraudulent, these systems rely on a variety of data points. For example, timestamps of SIM changes are critical. They help link the timing of a SIM swap to other suspicious activities, like login attempts or password resets.
Frequency data is another key indicator. Multiple SIM swaps within a short period often signal fraud, as legitimate users rarely switch SIM cards so frequently.
Device information is also scrutinized. By comparing the operating system, browser fingerprint, and hardware specs of a new device with historical data, the system can detect major discrepancies that may point to unauthorized access.
Location analytics play a big role too. If a SIM card is activated in a location that doesn’t match the user’s usual patterns, it raises an alert.
Correlating account activity with SIM swap events is particularly effective. For instance, if a SIM swap is quickly followed by several password reset attempts across different platforms, the system can recognize it as a likely attack.
Historical SIM data helps create a profile of typical behavior. This allows detection systems to flag unusual patterns, like a sudden increase in SIM swaps. Financial institutions use this data to add extra security checks before sending one-time passwords, blocking numbers that seem compromised based on their SIM swap history.
The need for robust detection is clear. Research shows that around 80% of SIM swap fraud attempts succeed [1]. In 2022 alone, the FBI reported $72 million in losses due to these attacks [10]. Monitoring for patterns like repeated failed login attempts after a SIM swap is also crucial, as this often indicates attackers are trying to exploit intercepted verification codes [12].
sbb-itb-070b8f8
How to Prevent SIM Swap Fraud
Preventing SIM swap fraud involves a mix of carrier-driven defenses and proactive actions by individuals and businesses. While detection systems help identify suspicious activity, prevention measures are designed to stop threats before they occur.
Carrier-Level Protections
Carriers have stepped up their security game, implementing advanced measures to counter the growing threat of SIM swap fraud. These protections focus on robust SIM management and enhanced verification processes.
Port Protection and SIM Locks
One of the most effective defenses carriers offer includes port protection and SIM locks. Businesses can work with mobile operators to enable "port-freeze" or "SIM-lock" features on corporate accounts. These measures require pre-set PINs or additional out-of-band approval for any port-out requests, making it much harder for fraudsters to hijack a phone number, even if they have access to personal information[4].
Advanced Monitoring Systems
Telecom providers also use advanced monitoring tools to detect unusual activity. By keeping an eye on telephony events and SS7 signaling, carriers can quickly flag unauthorized signaling queries or unexpected changes to IMSI (International Mobile Subscriber Identity) or ICCID (Integrated Circuit Card Identifier)[4]. Many carriers now collaborate with telecom fraud-detection services to provide real-time alerts for suspicious behavior.
Fraud tactics are constantly evolving, and carriers must adapt to meet these challenges. As AT&T puts it: “The best way to combat ever-evolving fraud tactics is to allow industry players the ability to adapt and respond to these changing threats in real-time”[15].
Steps for Individuals and Businesses
Both individuals and organizations can take practical steps to reduce their exposure to SIM swap fraud. By layering multiple security measures, it becomes significantly harder for attackers to succeed.
Account Security Basics
Start with the basics: create a strong, unique PIN for your wireless account. This PIN should only be known to authorized users. Additionally, download your carrier’s mobile app to stay updated on security features and alerts[2].
Stay Alert and Limit Exposure
Keep an eye on your account activity. If you notice that calls or texts suddenly stop working, contact your carrier immediately. To lower your risk, avoid sharing your phone number publicly whenever possible[2].
Rethink Authentication
SMS-based verification isn’t the most secure option. Instead, use authentication apps for two-factor authentication (2FA). These apps offer a safer alternative to SMS codes. When available, request callback verification for account changes – this ensures that any updates are confirmed via your registered phone number[13]. Also, avoid linking critical accounts, like banking or email, directly to your phone number.
Extra Security Features
Consider locking your account lines to prevent unauthorized SIM changes. Using strong, unique passwords for each of your online accounts adds another layer of protection. This way, even if one account is compromised, others remain secure[3][14].
Tailored Protections for Businesses
Businesses should conduct regular risk assessments. Techniques like device fingerprinting, geolocation checks, and monitoring login patterns can help identify and block suspicious activity. These steps are particularly useful for spotting unusual behavior during login or password-reset attempts[4].
Incident Response Planning
Prepare for potential breaches by having a clear incident response plan. This includes actions to take when alerts are triggered, minimizing damage and recovery time. Regular training and drills ensure that employees know how to follow these procedures effectively[12][4].
Ongoing Security Checks
Conduct regular audits of account activity to identify vulnerabilities early. Stay informed by following security advisories and updates, and make multi-factor authentication a standard practice to keep up with evolving threats[2].
Using JoltSMS to Improve SIM Swap Protection
JoltSMS takes SIM swap protection to the next level by isolating your SMS verification process from your primary phone number. Instead of relying on traditional methods, JoltSMS uses dedicated, non-VoIP numbers to reduce your exposure to SIM swap attacks. Below, we’ll explore how JoltSMS enhances security with its specialized features.
Benefits of JoltSMS for SIM Swap Prevention
JoltSMS provides real SIM-based U.S. numbers that offer greater security and dependability compared to VoIP alternatives. Since its launch in 2018, JoltSMS has processed over 402,000 SMS codes and issued more than 10,000 long-term numbers, demonstrating its reliability in handling SMS verification tasks[11].
Each JoltSMS number is private, dedicated, and never recycled during the rental period. This ensures that your number remains unique to you, as confirmed by JoltSMS:
"Your number is never shared; no personal data exposed." [11]
This privacy feature is crucial for SIM swap protection, as it eliminates the risk of inheriting a number tied to someone else’s accounts.
Reliability is another standout feature. With a 99.9% delivery rate, backed by carrier-grade SIM hardware, JoltSMS ensures your verification codes are delivered promptly when you need them most.
JoltSMS numbers are also widely accepted across over 1,000 platforms, including major services like Google, Coinbase, and WhatsApp, where VoIP numbers often fail. As the platform notes:
"Real SIM-Based US Numbers Accepted where VoIP fails – Google, WhatsApp, Telegram, Tinder, more." [11]
This broad compatibility allows you to secure multiple accounts using a single, dedicated number.
How JoltSMS Works
Here’s how JoltSMS simplifies and strengthens your SMS verification process. For a flat rate of $50 per month, you get a dedicated U.S. number with a minimum 30-day rental period. This cost includes unlimited inbound SMS under fair-use policies, covering standard two-factor authentication and account maintenance needs.
Once you rent a number, protection begins immediately. The system integrates seamlessly with tools like Slack or Discord through real-time webhooks, delivering SMS codes instantly. This feature is especially useful for managing multiple accounts. A customer from Grand Rapids, MI, shares their experience:
"As someone who has multiple VA’s, sharing multiple online accounts, this is a must-have tool. I have multiple long‑term numbers, each sending SMS verification codes to a shared slack channel. Very reliable!" [11]
You can also access your verification codes through a real-time dashboard, REST API, or webhook integration, making it easy to incorporate JoltSMS into your existing workflows.
For smooth operation, JoltSMS recommends using a U.S. IP address when verifying accounts with their numbers to avoid geolocation issues. If an SMS code is delayed, waiting 60 seconds before retrying is advised. In case of any issues, their 24/7 support team is ready to assist via help.joltsms.com, offering a money-back guarantee for failed SMS deliveries.
With auto-renewal in place, your number stays active without interruptions, ensuring consistent access to your accounts. If needed, cancellation is available anytime, giving you full control while maintaining reliable protection against SIM swap threats.
Conclusion
SIM swap detection has become increasingly critical as fraud skyrocketed by over 1,000% in 2024[4]. In the U.S. alone, criminals stole more than $100 million in cryptocurrency last year through these attacks[16].
SIM swap attacks work by bypassing SMS-based authentication, allowing criminals to take over digital identities. Once they gain control of a phone number, they can access bank accounts, emails, and social media profiles, leading to severe financial losses and reputational harm. This highlights the urgent need for proactive detection methods and stronger authentication tools.
Detecting these attacks early is crucial since the damage escalates rapidly once the attack is completed. Real-time monitoring systems can spot suspicious patterns and activate protective measures before attackers can fully exploit their access.
As Allison Nixon, Director of Research at Flashpoint, emphasizes:
"SIM swapping is proliferating, and it is going to keep proliferating until companies deal with this. I’ve been looking at the criminal underground for a long time, and SIM swapping bothers me more than anything I’ve seen." [18]
Key Takeaways
Protecting against SIM swap attacks requires a combination of preventive measures and quick responses from both individuals and organizations. The FBI reported nearly $50 million in losses from SIM swapping in just one year, highlighting the pressing need for action[17].
For individuals, safeguarding begins with reducing personal information shared on social media and setting up SIM card PINs or passwords to block unauthorized changes. Switching from SMS-based authentication to app-based or hardware token methods adds another layer of protection. Additionally, monitoring for warning signs like an unexpected loss of mobile service can help catch attacks early.
Businesses face even greater stakes, as they must secure their operations and protect customer data. Adopting authentication methods based on behavioral patterns and multi-factor systems that avoid SMS-based methods can significantly enhance security. Employee training to spot social engineering tactics and having robust incident response plans are equally essential.
AI-driven fraud management is emerging as a powerful tool in SIM swap defense. These systems analyze risk factors like location changes and behavioral anomalies to flag potential fraud before it escalates.
As SIM swap attacks grow more sophisticated, combining real-time monitoring, advanced authentication methods, and continuous user education is key to staying ahead of the threat. Solutions like JoltSMS offer a strong line of defense, integrating cutting-edge technology to combat this evolving risk effectively.
FAQs
How can I tell if my phone number has been affected by a SIM swap attack?
If you’ve fallen victim to a SIM swap attack, there are a few telltale signs to look out for. The most obvious? A sudden loss of mobile service. If your phone stops making calls, sending texts, or connecting to mobile data – while others around you have no issues – it could mean your SIM has been swapped. Another common clue is receiving unexpected alerts or messages from your mobile carrier about changes to your account, like a new SIM activation or number transfer you didn’t authorize.
You might also notice other suspicious activity, such as being locked out of your online accounts, spotting unauthorized transactions (like strange bank withdrawals or cryptocurrency transfers), or unusual behavior on your social media accounts. If you suspect this has happened, take immediate action: contact your mobile carrier to regain control of your number and alert your bank or financial institutions to secure your accounts. Time is critical in minimizing the damage.
What should I do if I think my phone number has been SIM swapped?
If you think your phone number has been SIM swapped, taking quick action is essential to safeguard your personal information and accounts.
Start by contacting your mobile carrier immediately. Let them know about the issue and ask them to secure your account. They’ll investigate and help you regain control of your number. Next, change the passwords for any online accounts tied to your phone number. Wherever possible, enable two-factor authentication (2FA) for an added layer of security.
Keep a close eye on your financial accounts for any suspicious activity. If needed, consider temporarily freezing them to prevent unauthorized access. It’s also a good idea to notify your bank and other key institutions about the potential fraud. This way, they can help protect your assets. Acting fast can make a big difference in minimizing the damage from a SIM swap attack.
Which industries and accounts are most at risk of SIM swap fraud?
Certain industries and account types face a greater threat from SIM swap fraud, primarily because they depend heavily on mobile phones for handling sensitive activities like transactions and authentication. Sectors such as finance, healthcare, mobile gambling, and lottery services are particularly attractive to attackers, as these industries often involve access to personal data, financial records, or other valuable assets.
Accounts linked to financial platforms, social media, or cryptocurrency wallets are especially vulnerable. Cybercriminals frequently target these accounts to intercept two-factor authentication (2FA) codes, enabling them to take over the accounts. Implementing robust security measures for these accounts is critical to minimizing the risk of such attacks.