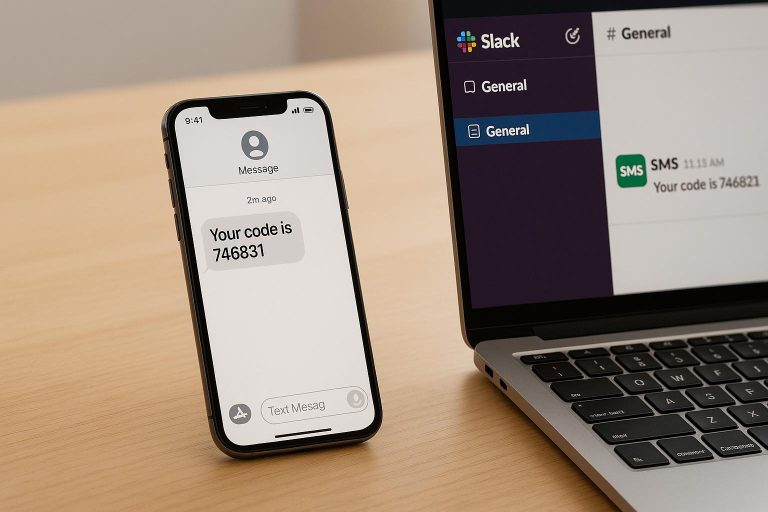
How eSIMs Help Stop SIM Swap Fraud
SIM swap fraud is on the rise, but eSIM technology offers a better way to protect your mobile identity. Unlike traditional SIM cards, eSIMs are embedded directly into your device and activated remotely, making them harder to steal or tamper with. Here’s why eSIMs are a strong defense against SIM swap fraud:
- No physical SIM card to steal: eSIMs are built into your device, eliminating the risk of theft or unauthorized replacement.
- Stronger authentication: Carriers use stricter identity verification and tie eSIM profiles to specific devices, reducing fraud risks.
- Real-time monitoring: eSIMs enable carriers to detect suspicious activity, like unusual location changes or repeated activation attempts.
- Remote management: Compromised eSIM profiles can be deactivated instantly without needing physical intervention.
eSIMs aren’t just safer – they’re also more convenient. You can switch carriers remotely without waiting for a new SIM card. By combining eSIMs with additional security measures like multi-factor authentication, you can significantly reduce the chances of falling victim to SIM swap fraud.
Can eSIM protect SIM swap frauds in India?
What Are eSIMs and How Do They Work?
To understand how eSIMs help protect against SIM swap fraud, it’s important to first grasp what they are and how they differ from the traditional SIM cards we’re all familiar with. eSIMs change the game by removing the need for a physical card altogether, offering a modern take on mobile connectivity. Knowing these basics helps explain why they’re a strong defense against SIM swap fraud.
eSIM Technology Basics
An eSIM, or embedded SIM, is a digital SIM card that’s built directly into your device’s hardware. Unlike the small plastic SIM cards you insert into a phone, eSIMs are permanently installed in your device. This means there’s no SIM card slot or tray that can be misplaced or damaged.
What sets eSIMs apart is their ability to be programmed remotely. Instead of heading to a carrier store to pick up a new SIM card, you can simply download your carrier’s profile directly onto your device using a process called Remote SIM Provisioning (RSP).
The adoption of eSIM technology is growing fast. Over 500 million eSIMs are already active worldwide [7], and as of 2023, more than 200 mobile carriers support this technology [9]. By 2025, experts predict that half of all smartphones shipped will be eSIM-compatible [9].
Because eSIMs are embedded in the device and activated remotely, they eliminate many of the risks associated with traditional SIM cards, such as theft or physical tampering.
eSIMs vs Physical SIMs: Main Differences
The differences between eSIMs and traditional SIM cards go beyond their physical design. These differences have major implications for security, convenience, and even fraud prevention.
Physical Security:
Traditional SIM cards are small and removable, making them easy to lose, steal, or damage [7]. eSIMs, on the other hand, are embedded within the device and can’t be physically removed, offering better protection against theft [10][11].
Activation Process:
Switching carriers with a physical SIM often requires a trip to the store or waiting for a new card to arrive in the mail. Someone also has to physically insert or remove the card. eSIMs eliminate all of that hassle. They can be activated remotely, reducing the risk of theft or interception during delivery [5][6][11].
Device Design:
Since eSIMs are built directly into devices, they free up internal space. This allows manufacturers to create smaller devices or add features like larger batteries – an especially big deal for compact gadgets like smartwatches [5][8].
| Feature | Physical SIM | eSIM |
|---|---|---|
| Installation | Removable plastic card | Embedded chip inside device |
| Carrier Switching | Requires physical swapping | Switch carriers remotely |
| Physical Security | Can be lost or damaged | Cannot be physically removed |
| Fraud Risk | Vulnerable to SIM swapping | Enhanced security measures |
Compatibility:
Physical SIM cards work with nearly every mobile carrier and device [5]. While eSIMs are currently limited to newer devices [5], this gap is closing quickly as the technology becomes more widely adopted.
The design and functionality of eSIMs make them a much safer option when it comes to protecting against SIM swap fraud. Their remote activation and embedded nature add layers of security that traditional SIM cards simply can’t match.
How eSIMs Stop SIM Swap Fraud
Thanks to the built-in security features of eSIM technology, carriers have developed advanced digital defenses that tackle SIM swap fraud head-on. By addressing the weaknesses of traditional SIM cards, eSIMs create multiple layers of protection, making it far tougher for fraudsters to hijack your phone number. Here’s a closer look at how eSIMs enhance security.
Carrier Authentication and Secure Setup
Activating an eSIM involves stricter identity verification than the process for traditional SIM cards. Carriers use multi-layer authentication protocols that go well beyond the basic checks typically associated with physical SIMs. This setup includes encrypted digital profiles that are securely tied to your device and account, forming a unique digital fingerprint that resists cloning and theft [12][13]. Many carriers also enforce stringent Know Your Customer (KYC) procedures and bind eSIM profiles to specific device hardware IDs, further reducing the risk of fraudulent activity [4].
The effectiveness of these measures is driving widespread adoption. In fact, the global eSIM market is expected to grow at an annual rate of 13.5% through 2025 [3]. These authentication practices lay the groundwork for even more advanced digital protections.
No Physical SIM Card to Steal or Replace
One of the standout advantages of eSIMs is the absence of a physical card. Traditional SIM swap fraud often relies on criminals either stealing a SIM card or tricking carriers into issuing a replacement. With eSIMs embedded directly into devices, this physical vulnerability is completely removed, making unauthorized swaps significantly harder to pull off.
This added layer of physical security is especially important given the rising number of SIM swap fraud cases. Recent FBI data revealed 2,026 reported incidents in 2022, resulting in losses exceeding $72 million [1]. While digital attacks are still possible, they require breaching the robust systems carriers have put in place [12].
Real-Time Monitoring and Account Locks
To complement the secure setup process, carriers now use real-time monitoring to detect and respond to potential threats. eSIMs allow for advanced security features that weren’t feasible with physical SIM cards. For instance, carriers can track unusual activity, such as sudden changes in location or repeated activation attempts, and flag these as potential fraud before any damage is done. Features like SIM-locks and port-freezes can also lock your phone number in place, preventing unauthorized transfers [13]. In some cases, carriers may temporarily disable eSIM functionality if a device has been recently unlocked as a precaution [14].
Thanks to remote management capabilities, carriers can instantly deactivate compromised profiles and issue replacements without requiring physical intervention. On top of that, machine learning and fraud analytics tools analyze account activity across millions of users to identify suspicious patterns that might escape human detection [4].
While no system is entirely foolproof, eSIMs significantly reduce the risk of SIM swap fraud. By combining stronger authentication, eliminating physical vulnerabilities, and enabling real-time monitoring, eSIMs make it far more difficult for fraudsters to succeed compared to traditional SIM cards.
sbb-itb-070b8f8
Building Better Security With eSIMs and Other Protections
eSIMs offer a strong defense against SIM swap fraud, but they shine brightest when paired with a well-rounded security strategy. The key lies in combining eSIM technology with other protective measures to create layers of security that can thwart cyberattacks more effectively.
By integrating robust multi-factor authentication (MFA) and continuous monitoring, organizations can significantly enhance their security posture.
Using eSIMs With Multi-Factor Authentication
Pairing app-based and biometric authentication with eSIM technology creates a formidable first line of defense. While traditional SMS-based two-factor authentication (2FA) becomes more secure with eSIMs, incorporating authenticator apps or biometric verification takes security to the next level.
"eSIM two-factor authentication stands at the forefront of secure, efficient, and convenient digital access… It strengthens defenses against evolving cyber threats, safeguarding user safety and data protection." – Yevhenii Kuznietsov, Author [16]
Businesses can further enhance security by integrating API authentication methods like OAuth and OpenID Connect with eSIM-based 2FA. These integrations add an extra layer of protection during API transactions. Similarly, protocols such as LDAP and EAP work seamlessly with eSIM 2FA systems, ensuring that only authorized users can access sensitive resources [16]. Device fingerprinting adds another layer by binding eSIM profiles to specific hardware, ensuring access remains tied to individual users.
Even if attackers manage to compromise one layer of authentication, the combination of eSIM and MFA makes it significantly harder for them to gain full account access.
Organizations should also explore adaptive MFA, which adjusts security requirements based on the level of risk. For instance, users logging in from familiar devices and locations might face fewer challenges, while unusual login attempts would trigger additional verification steps [17].
Beyond authentication, monitoring user behavior is critical for detecting threats early.
Monitoring User Behavior and Risk Patterns
Real-time behavioral analysis is becoming a crucial tool in preventing fraud. Advanced AI systems monitor eSIM usage patterns in real time, flagging suspicious activities that could indicate fraud attempts. These systems can identify anomalies such as unusually high call volumes from a single device, multiple activations across different regions, or usage patterns that deviate from a user’s normal behavior [4][19].
As fraud evolves, researchers have uncovered cases of criminals selling eSIM contracts on the dark web. These contracts are often registered with fake details or through intermediaries like money mules, with regions such as Hong Kong, Japan, and the United States being common points of origin [19].
Device fingerprinting plays a vital role here by linking eSIM profiles to unique hardware IDs. This prevents cloning or unauthorized reuse across devices, making it harder for fraudsters to transfer stolen credentials. Continuous monitoring of device identifiers and behavior patterns can help detect and block devices attempting to spoof identities or rapidly switch profiles [4].
For individuals, staying alert to unusual account activity is equally important. Enable login attempt notifications, regularly check your accounts, and report any suspicious behavior immediately. On a broader scale, organizations should deploy monitoring systems capable of analyzing data patterns to detect potential fraud before serious damage occurs [18].
Use Case: Dedicated Phone Numbers for SMS Verification
eSIMs are a great way to protect against SIM swap fraud, but sometimes businesses and individuals need a separate solution for handling SMS verification. Having dedicated phone numbers for this purpose adds an extra layer of security by keeping verification activities separate from your personal or business communications.
Plenty of services require a real mobile number for account verification [20]. But using your personal number for these verifications can lead to privacy issues, spam, and even security risks. Virtual phone numbers solve this problem by letting you receive SMS verification codes without exposing your actual contact information [21]. For instance, JoltSMS provides dedicated numbers that prioritize security and privacy during the verification process.
JoltSMS: Dedicated SMS Verification Numbers
JoltSMS complements eSIM technology by offering real, SIM-based U.S. numbers specifically for long-term SMS verification. These numbers use carrier-grade SIM hardware, ensuring they work seamlessly with a wide range of platforms.
For $50 per month (with a minimum 30-day rental), you get a dedicated U.S. number that supports over 1,000 platforms, including major services like Google, Coinbase, WhatsApp, and various banking apps – all without any per-message fees. Your number is private, never shared, and not recycled during the rental period, so you don’t have to worry about previous users’ activities interfering with your verification attempts. As JoltSMS emphasizes:
"Privacy is Our First Principle. Never share your personal number; we store only the data needed to verify you." [22]
JoltSMS also offers team-friendly features, such as instant SMS delivery through Slack or Discord webhooks, a real-time dashboard, and a REST API. This setup eliminates the need to manually share verification codes, reducing the risks tied to forwarding sensitive authentication messages. When combined with eSIM-enabled devices, these dedicated numbers provide an even stronger separation between your primary communications and verification traffic.
With a 99.9% SMS delivery rate, backed by carrier-grade SIM hardware, JoltSMS ensures reliable performance [22]. They also provide 24/7 human support and offer money-back guarantees for failed SMS deliveries, making it a dependable choice for businesses handling critical verification needs.
"To give individuals and teams a reliable, private alternative to disposable VoIP numbers – so you never have to hand out your personal phone number, risk spam texts, or expose your identity online. With JoltSMS, every account stays verified, secure, and truly yours." – JoltSMS [22]
Conclusion: How eSIMs Fight SIM Swap Fraud
eSIM technology strengthens the fight against SIM swap fraud by tackling the weaknesses that make traditional SIM cards vulnerable to criminals.
Because eSIMs are embedded directly into devices, they remove the need for physical SIM cards – a common target for fraudsters. They also introduce stricter authentication processes for activation and transfers, rely on advanced encryption to protect subscriber data, and can be remotely deactivated if a device is lost or stolen [11][15][23].
While eSIMs offer a stronger line of defense, no technology is entirely immune to attacks [2]. For the best protection, eSIMs should be paired with additional security measures like multi-factor authentication and dedicated verification numbers, such as those provided by JoltSMS. This layered approach creates multiple hurdles for potential fraudsters.
As threats like SIM swapping continue to evolve, eSIMs provide a more secure starting point for mobile communication. However, they work most effectively as part of a broader security strategy that addresses various attack methods simultaneously.
FAQs
How does activating an eSIM differ from a physical SIM, and what security benefits does it provide?
Activating an eSIM is a completely digital process, usually done by scanning a QR code or using a mobile app from your carrier. Unlike traditional SIM cards that require physically inserting or swapping a chip, eSIMs are already embedded into your device, eliminating the need to handle any hardware.
This built-in design brings notable security perks. Because eSIMs can’t be physically removed, they’re much harder to steal or manipulate, which helps prevent SIM swap fraud – a tactic where hackers take control of your phone number to access personal accounts. On top of that, eSIMs often rely on advanced encryption and authentication measures, adding an extra layer of protection against unauthorized access.
How can I improve the security of my mobile device when using an eSIM?
To keep your mobile device safe while using an eSIM, start by enabling two-factor authentication (2FA) for your eSIM profile and any connected accounts. This adds an extra security step, making it harder for others to gain unauthorized access.
Always use strong and unique passwords for your accounts, and make it a habit to update them regularly. Keep your device’s operating system and apps updated, as updates often include important security patches. Be cautious with links or files from unknown sources, and consider installing reliable anti-malware software to protect against potential threats.
Taking these precautions can help you better secure your mobile device and minimize the chances of any breaches.
Are there any potential challenges or compatibility issues to consider when switching from a traditional SIM card to an eSIM?
While eSIM technology comes with plenty of perks, there are a few challenges you should consider when moving away from a traditional SIM card. For starters, not all devices are equipped to handle eSIMs, so it’s crucial to check if your smartphone, tablet, or wearable is compatible. On top of that, some carriers might not fully support eSIM functionality yet, which could limit your choices depending on your location or service provider.
If you’re someone who likes to switch between phones often, using an eSIM might feel a bit less straightforward than simply swapping out a physical SIM card. That said, many carriers now offer online tools to make this process easier. To avoid any hiccups, take the time to confirm both your device’s compatibility and your carrier’s eSIM support before making the switch.